Excel in Web Application
Security Testing with

Excel in Web Application
Security Testing with

Enroll now to get details on Plans & Pricing
EC-Council’s Web Application Hacking and Security is a specialization certification that enables you to play, learn, hack, test, and secure web applications from existing and emerging security threats in the industry verticals.

Web Application Hacking and Security has challenges derived from the engaging iLab environments of EC Council – from Certified Ethical Hacker (CEH) to the Certified Penetration Testing Professional (CPENT); from Certified Application Security Engineer (CASE) .Net to Java. But Web Application Hacking and Security goes beyond this to more difficult scenarios as you advance through each problem.
Web Application Hacking and Security is like a Capture-The-Flag (CTF) competitions meant to test your hacking skills. But you can keep on trying until you achieve the goal. Test your skills and work alone to solve complex problems or follow the instructor as they do a walkthrough to help you learn Web Application Hacking and Security.
Watch your name rise on the leader board, a place where you’ll see who’s cracking the most challenges, who’s making the most progress, who’s cranking out the h@ck$!
Why WAHS Is Your Go-to Certification for Web Application Security Testing?
Web Application Hacking and Security is the only experiential program that provides comprehensive knowledge and 100% hands-on learning. It helps cybersecurity professionals to learn, hack, test, and secure web applications from existing and emerging security threats. Learn about application vulnerabilities and web application hacking concepts through this course designed by experts.
100% Performance based Course!
No Death by PowerPoint!
Learn by Doing!
Step By Step Video Instruction
Test your skills and learn to excel in web application security testing. Whether you are a beginner, or an experienced ethical hacker, Web Application Hacking and Security course offers something for all skill levels.
Program Information
- Challenges
- Course Outline
- Break The Code
- Exam Outcomes
- Brochure
Level up your Skills through Play
Challenges
You will encounter security misconfigurations, SQL injection vulnerabilities, directory browsing vulnerabilities, enumeration vulnerabilities, and opportunities to escalate privileges and gain access to privileged information.
Each section of ‘Break the Code’ brings progressively more difficult challenges. There are always multiple paths to take, but few will get you the prize and move up the leader board.

Learn by Doing
How You Will Learn:
Complete Walkthrough Instruction & Challenge Based Environment
Unlike many Capture-the-Flag challenges and Vulnerable Virtual Machines, Web Application Hacking and Security provides the challenger with the ability to follow an instructor as they make their way through the challenges. The instructor will present alternatives, do scans, upload malicious payloads, and crack passwords from their home computer just like you.
– But don’t rely on the walkthrough; challenge yourself and see how far you can get. Play some of the walkthroughs, then pause and try some more.
In the process, you will learn about application vulnerabilities and web application hacking. Even though this will prove useful for other CTF contests, and in cracking VVMs, it will be even more useful to your career as you learn to defend your applications and progress to Web Application Hacking and Security.
What you will learn:
Hack Your Way to Greatness!







Prove Your Skills – Become A Certified Web Application Security Associate, A Professional, or An Expert
Web Application Hacking and Security Exam Description
The Web Application Hacking and Security program leads to a fully online, remotely proctored practical exam that challenges candidates through a grueling 6-hour performance-based, hands-on exam. The exam assesses candidates’ skills and proficiency on a broad spectrum of OWASP Top-10 web application vulnerabilities and attack vectors. The assessment is not limited to only understanding of automated exploitation frameworks but requires a deep understating of various web application technologies, their inherent and acquired vulnerabilities, and manual exploitation techniques.
The exam focuses on candidates’ proficiency in performing a web application security assessment in real life stressful scenario. Candidates who score more than 60% will earn the Certified Web Application Security Associate certification, candidates who score more than 75% will be awarded the Certified Web Application Professional certification and candidates who score more than 90% attain the prestigious Certified Web Application Expert certification!
Web Application Hacking and Security Exam Process Overview
Web Application Hacking and Security Exam is a fully online, remotely proctored practical exam that challenges candidates through a grueling 6-hour performance-based, hands-on exam.
- The Web Application Hacking and Security exam dashboard will be available for 30 days from your Aspen account. Launch your Exam Dashboard when you are ready to take on the exam.
- You will need to schedule the exam sessions and clear the exam from the Exam Dashboard within the validity period of 30 days.
- You will need a host machine with a virtual machine running your penetration testing toolkit to take the exam. Please read the Host System Requirement and Virtual Machine Resource Requirement sections below carefully.
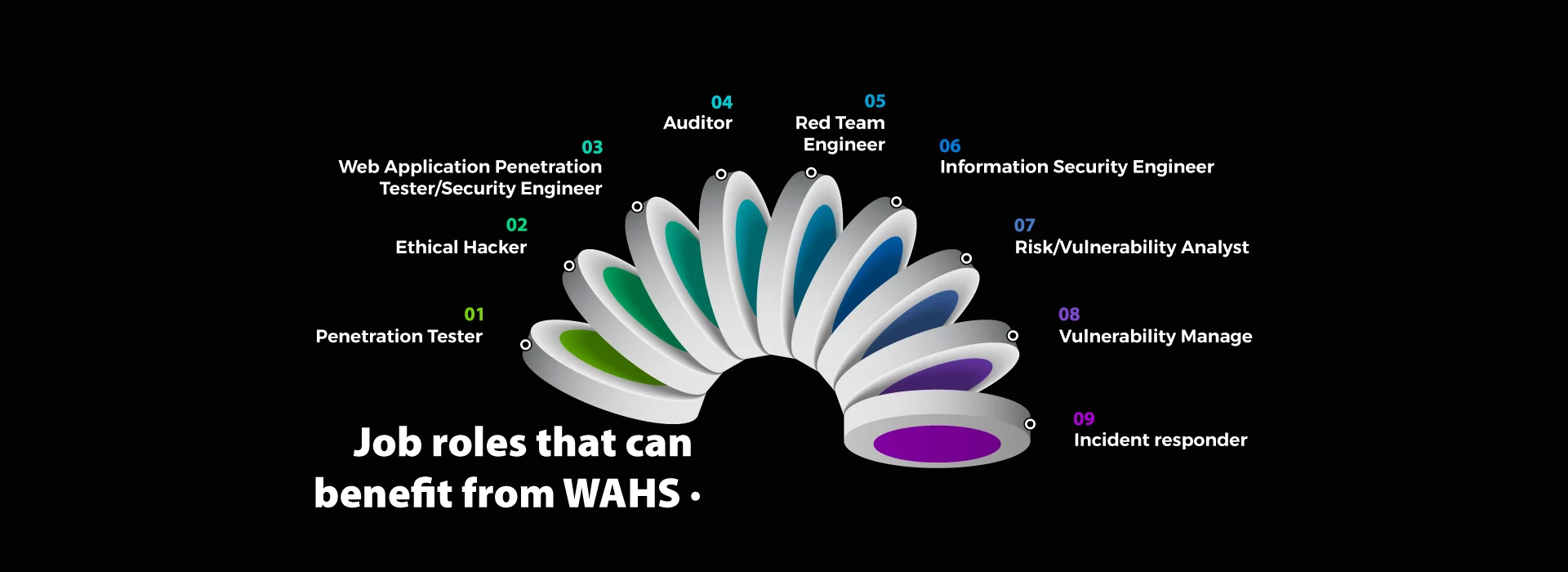
Who Should Attend?
If you are tasked with implementing, managing, or protecting web applications, then this course is for you. If you are a cyber or tech professional who is interested in learning or recommending mitigation methods to a myriad of web security issues and want a pure hands-on program, then this is the course you have been waiting for.