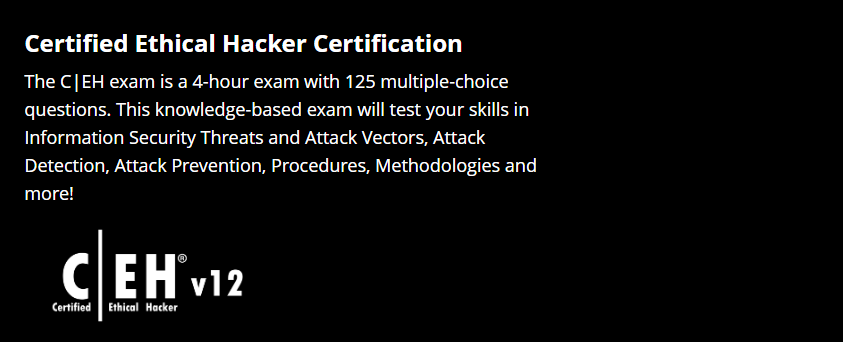
Cybersecurity Incidents Are Exploding.
So Are Cyber Jobs!
Build Your Career With the Most In-Demand Ethical Hacking Certification in the World, Certified Ethical Hacker
The World’s Number 1 Ethical Hacking Certification
A Structured Professional Course for Aspiring Cyber Professionals
Work Anywhere With C|EH- It’s Globally Recognized
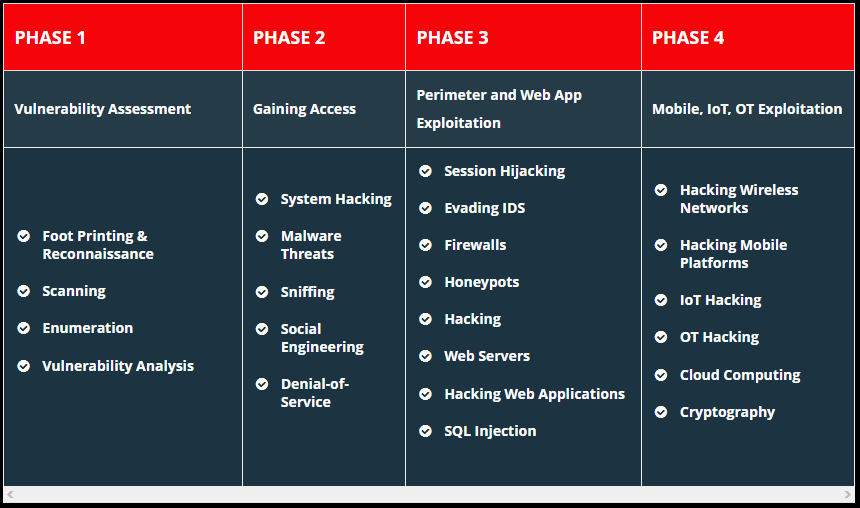
Comprehensive Program to Master the 5 Phases of Ethical Hacking
Hands-On Learning With CyberQTM
Flexible Learning Options : Live, Online, or Hybrid
The Encyclopedia of Ethical Hacking
How C|EH v12 Empowers You:
Unique Learn, Certify, Engage and Compete Methodology for Aspiring Cyber Professionals
Learn Ethical Hacking in a Structured Setting Across 20 Domains
Build Skills With over 220 Challenge-Based, Hands-On Labs with CyberQTM Labs
Gain Experience With over 500 Unique Attack Techniques
Learn Commercial-Grade Hacking Tools and Techniques
Engage: “Hack” a Real Organization With C|EH® Elite to Get Experience
Compete With Hackers Around the World as Part of the C|EH® Elite Program
Attain the Most Recognized Credential in the Cybersecurity Industry :C|EH®
A Revolutionary Way to Learn Ethical Hacking
Our exclusive Learn | Certify | Engage | Compete framework covers not only a comprehensive training program to prepare you for the certification exam, but also the industry’s most robust, in-depth, hands-on lab experience of any cybersecurity program available. C|EH v12 will teach you the latest commercial-grade hacking tools, techniques, and methodologies used by hackers and information security professionals to lawfully hack an organizations.




- What's New in C|EH v12
- Course Outline
- Who is it for?
- Brochure
- Learn
- Certify
- Engage
- Compete
What You Will Learn
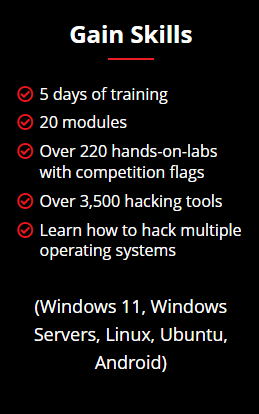
C|EH is divided into 20 modules and delivered through a carefully curated training plan that typically spans across 5 days. As you progress through your training, each module offers extensive hands-on lab components that allow you to practice the techniques and procedures taught in the program in real-time on live machines.
Ethical Hacking Labs
With over 220 hands-on labs, conducted in our cyber range environment, you will have the opportunity to practice every learning objective in the course on live machines and vulnerable targets. Pre-loaded with over 3,500 hacking tools and a variety of operating systems, you will gain unprecedented exposure to and hands-on experience with the most common security tools, latest vulnerabilities, and widely used operating systems on the market. Our range is web accessible, allowing you to study and practice from anywhere with a connection.
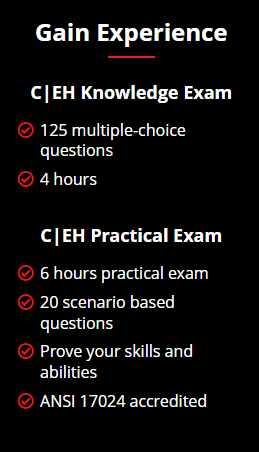
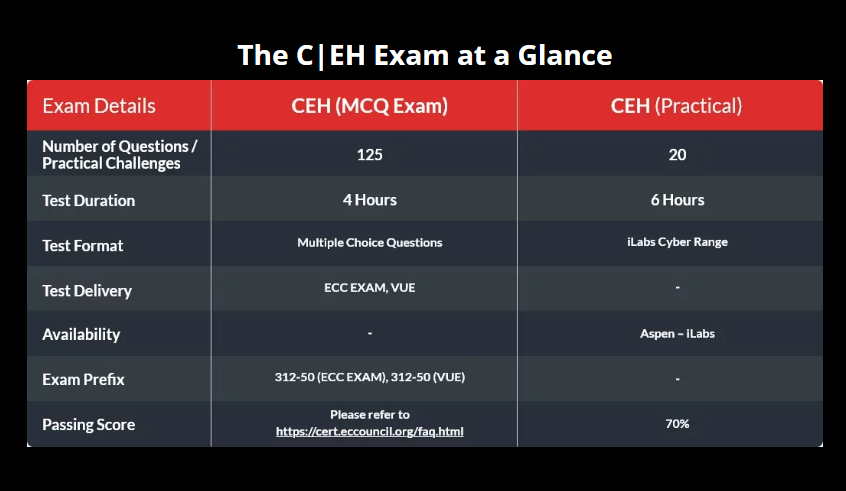
How You Will Get Certified
Prove Your Skills and Abilities With Online, Practical Examinations



How You Will Engage
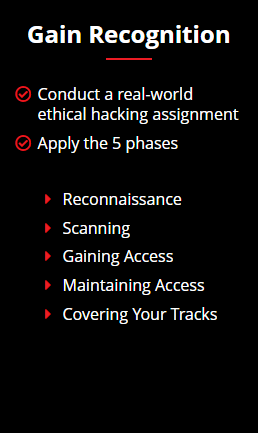
The C|EH v12 program helps you develop real-world experience in ethical hacking through the hands-on C|EH practice environment. C|EH Engage equips you with the skills to prove that you have what it takes to be a great ethical hacker.
Your security assessment objectives will be presented as a series of flags (questions you must answer in the Cyber Range by performing ethical hacking activities on the target organization).
New to C|EH v12, students will embark on their first emulated ethical hacking engagement. This 4-phase engagement requires students to think critically and test the knowledge and skills gained by capturing a series of flags in each phase, demonstrating the live application of skills and abilities in a consequence-free environment through EC-Council’s new Cyber Range.
As you complete your training and hands-on labs, C|EH Engage lets you apply everything you have learned in a mock ethical hacking engagement. This 4-part security engagement gives you a real ethical hacking engagement experience from start to finish against an emulated organization. Using our capture-the-flag-style range, you will complete your engagement by answering “flag” questions as you progress.
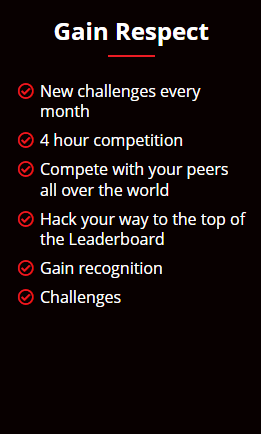
Where You Will Compete
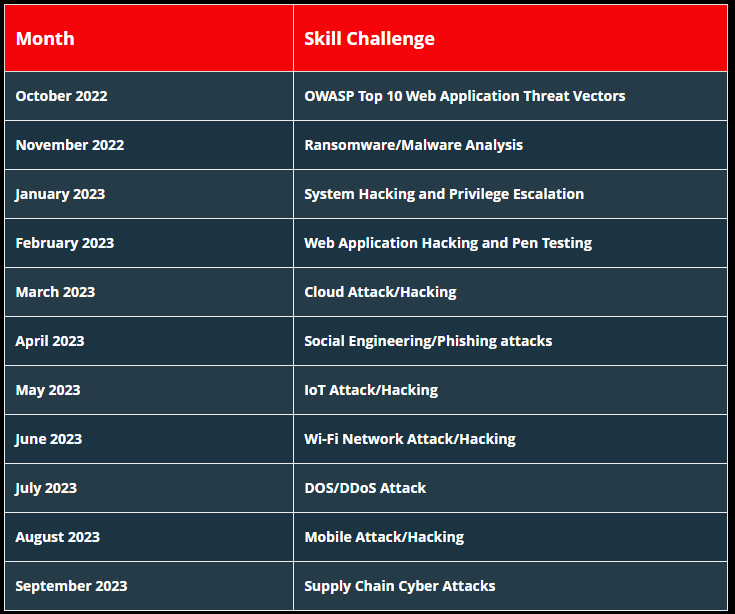
The C|EH Global Challenges occur every month, providing capture-the-flag style competitions that expose students to various new technologies and platforms, from web applications, OT, IoT, SCADA, and ICS systems to cloud and hybrid environments. Our Compete structure lets ethical hackers fight their way to the top of the leaderboard each month in these 4-hour curated CTFs. Objective-based flags are designed around the ethical hacking process, keeping skills current, testing critical thinking abilities, and covering the latest vulnerabilities and exploits as they are discovered. Hosted 100% online in EC-Council’s Cyber Range, candidates race the clock in scenario-based engagements against fully developed network and application environments with real operating systems, real networks, tools, and vulnerabilities to practice, engage, compete, build, and hone their cyber skills against various new target organizations.
New Challenges Every Month
- Learn
- Certify
- Engage
- Compete
What You Will Learn
C|EH is divided into 20 modules and delivered through a carefully curated training plan that typically spans across 5 days. As you progress through your training, each module offers extensive hands-on lab components that allow you to practice the techniques and procedures taught in the program in real-time on live machines.
Ethical Hacking Labs
With over 220 hands-on labs, conducted in our cyber range environment, you will have the opportunity to practice every learning objective in the course on live machines and vulnerable targets. Pre-loaded with over 3,500 hacking tools and a variety of operating systems, you will gain unprecedented exposure to and hands-on experience with the most common security tools, latest vulnerabilities, and widely used operating systems on the market. Our range is web accessible, allowing you to study and practice from anywhere with a connection.
How You Will Get Certified
Prove Your Skills and Abilities With Online, Practical Examinations





How You Will Engage
The C|EH v12 program helps you develop real-world experience in ethical hacking through the hands-on C|EH practice environment. C|EH Engage equips you with the skills to prove that you have what it takes to be a great ethical hacker.
Your security assessment objectives will be presented as a series of flags (questions you must answer in the Cyber Range by performing ethical hacking activities on the target organization).
New to C|EH v12, students will embark on their first emulated ethical hacking engagement. This 4-phase engagement requires students to think critically and test the knowledge and skills gained by capturing a series of flags in each phase, demonstrating the live application of skills and abilities in a consequence-free environment through EC-Council’s new Cyber Range.
As you complete your training and hands-on labs, C|EH Engage lets you apply everything you have learned in a mock ethical hacking engagement. This 4-part security engagement gives you a real ethical hacking engagement experience from start to finish against an emulated organization. Using our capture-the-flag-style range, you will complete your engagement by answering “flag” questions as you progress.

Where You Will Compete
The C|EH Global Challenges occur every month, providing capture-the-flag style competitions that expose students to various new technologies and platforms, from web applications, OT, IoT, SCADA, and ICS systems to cloud and hybrid environments. Our Compete structure lets ethical hackers fight their way to the top of the leaderboard each month in these 4-hour curated CTFs. Objective-based flags are designed around the ethical hacking process, keeping skills current, testing critical thinking abilities, and covering the latest vulnerabilities and exploits as they are discovered. Hosted 100% online in EC-Council’s Cyber Range, candidates race the clock in scenario-based engagements against fully developed network and application environments with real operating systems, real networks, tools, and vulnerabilities to practice, engage, compete, build, and hone their cyber skills against various new target organizations.
New Challenges Every Month

Course Outline
Course Outline
20 Modules that help you master the foundations of
Ethical Hacking and prepare to challenge the CEH certification exam.
20 Modules that help you master the foundations of Ethical Hacking and prepare to challenge the CEH certification exam.
Learn how to use the latest techniques and tools to perform foot printing and reconnaissance, a critical pre-attack phase of the ethical hacking process.
Over 30 hands-on exercises with real-life simulated targets to build skills on how to:
- Perform foot printing on the target network using search engines, web services, and social networking sites
- Perform website, email, whois, DNS, and network foot printing on the target network
Over 10 hands-on exercises with real-life simulated targets to build skills on how to:
- Perform host, port, service, and OS discovery on the target network
- Perform scanning on the target network beyond IDS and firewall
Over 20 hands-on exercises with real-life simulated targets to build skills on how to:
- Perform NetBIOS, SNMP, LDAP, NFS, DNS, SMTP, RPC, SMB, and FTP Enumeration
Over 5 hands-on exercises with real-life simulated targets to build skills on how to:
- Perform vulnerability research using vulnerability scoring systems and databases
- Perform vulnerability assessment using various vulnerability assessment tools
Over 25 hands-on exercises with real-life simulated targets to build skills on how to:
- Perform Online active online attack to crack the system’s password
- Perform buffer overflow attack to gain access to a remote system
- Escalate privileges using privilege escalation tools
- Escalate privileges in linux machine
- Hide data using steganography
- Clear Windows and Linux machine logs using various utilities
- Hiding artifacts in Windows and Linux machines
Get an introduction to the different types of malware, such as Trojans, viruses, and worms, as well as system auditing for malware attacks, malware analysis, and countermeasures.
Over 20 hands-on exercises with real-life simulated targets to build skills on how to:
- Gain control over a victim machine using Trojan
- Infect the target system using a virus
- Perform static and dynamic malware analysis
Learn about packet-sniffing techniques and how to use them to discover network vulnerabilities, as well as countermeasures to defend against sniffing attacks.
Over 10 hands-on exercises with real-life simulated targets to build skills on how to:
- Perform MAC flooding, ARP poisoning, MITM and DHCP starvation attack
- Spoof a MAC address of Linux machine
- Perform network sniffing using various sniffing tools
- Detect ARP poisoning in a switch-based network
Learn social engineering concepts and techniques, including how to identify theft attempts, audit human-level vulnerabilities, and suggest social engineering countermeasures.
Over 4 hands-on exercises with real-life simulated targets to build skills on how to:
- Perform social engineering using Various Techniques
- Spoof a MAC address of a Linux machine
- Detect a phishing attack
- Audit an organization’s security for phishing attacks
Learn about different Denial-of-Service (DoS) and Distributed DoS (DDoS) attack techniques, as well as the tools used to audit a target and devise DoS and DDoS countermeasures and protections.
Over 5 hands-on exercises with real-life simulated targets to build skills on how to:
- Perform a DoS and DDoS attack on a target host
- Detect and protect against DoS and DDoS attacks
Understand the various session hijacking techniques used to discover network-level session management, authentication, authorization, and cryptographic weaknesses and associated countermeasures.
Over 4 hands-on exercises with real-life simulated targets to build skills on how to:
- Perform session hijacking using various tools
- Detect session hijacking
Get introduced to firewall, intrusion detection system, and honeypot evasion techniques; the tools used to audit a network perimeter for weaknesses; and countermeasures.
Over 7 hands-on exercises with real-life simulated targets to build skills on how to:
- Bypass Windows Firewall
- Bypass firewall rules using tunneling
- Bypass antivirus
Over 8 hands-on exercises with real-life simulated targets to build skills on how to:
- Perform web server reconnaissance using various tools
- Enumerate web server information
- Crack FTP credentials using a dictionary attack
Over 15 hands-on exercises with real-life simulated targets to build skills on how to:
- Perform web application reconnaissance using various tools
- Perform web spidering
- Perform web application vulnerability scanning
- Perform a brute-force attack
- Perform Cross-Site Request Forgery (CSRF) Attack
- Identify XSS vulnerabilities in web applications
- Detect web application vulnerabilities using various web application security tools
Over 4 hands-on exercises with real-life simulated targets to build skills on how to:
- Perform an SQL injection attack against MSSQL to extract databases
- Detect SQL injection vulnerabilities using various SQL injection detection tools
Over 3 hands-on exercises with real-life simulated targets to build skills on how to:
- Foot Print a wireless network
- Perform wireless traffic analysis
- Crack WEP, WPA, and WPA2 networks
- Create a rogue access point to capture data packets
Over 5 hands-on exercises with real-life simulated targets to build skills on how to:
- Hack an Android device by creating binary payloads
- Exploit the Android platform through ADB
- Hack an Android device by creating APK file
- Secure Android devices using various Android security tools
Over 2 hands-on exercises with real-life simulated targets to build skills on how to:
- Gather information using Online foot printing tools
- Capture and analyze IoT device traffic
Over 5 hands-on exercises with real-life simulated targets to build skills on how to:
- Perform S3 Bucket enumeration using various S3 bucket enumeration tools
- Exploit open S3 buckets
- Escalate IAM user privileges by exploiting misconfigured user policy
Over 10 hands-on exercises with real-life simulated targets to build skills on how to:
- Calculate MD5 hashes
- Perform file and text message encryption
- Create and use self-signed certificates
- Perform email and disk encryption
- Perform cryptanalysis using various cryptanalysis tools
Common Job Roles for C|EH
Mid-Level Information Security Auditor
Cybersecurity Analyst level 1, level 2, & level 3
Cybersecurity Auditor
Network Security Engineer
Security Administrator
SOC Security Analyst
IT Security Administrator
Security Analyst
Cyber Defense Analyst
Network Engineer
Vulnerability Assessment Analyst
Senior Security Consultant
Warning Analyst
Information Security Manager
Information Security Analyst 1
Senior SOC Analyst
Security Analyst L1
Solution Architect
Infosec Security Administrator
Cybersecurity Consultant
Common Job Roles for C|EH
Making an informed decision is difficult, and that’s where EC-Council’s C|EH brochure comes to your rescue. The Certified Ethical Hacker (CEH) credential is the most trusted ethical hacking certification that employers worldwide value, and for good reasons.
The comprehensive curriculum covers the fundamentals of ethical hacking, foot printing and reconnaissance, scanning, enumeration, vulnerability threats, social engineering, SQL injection, and much more.
When you successfully achieve the C|EH certification, you will be equipped with every skill you need to uncover vulnerabilities and secure the systems, networks, applications, databases, and critical data from malicious hackers.
This is only an overview of C|EH and what you will learn.
For complete information, download the brochure now.

- Learn
- Certify
- Engage
- Compete
What You Will Learn
C|EH is divided into 20 modules and delivered through a carefully curated training plan that typically spans across 5 days. As you progress through your training, each module offers extensive hands-on lab components that allow you to practice the techniques and procedures taught in the program in real-time on live machines.
Ethical Hacking Labs
With over 220 hands-on labs, conducted in our cyber range environment, you will have the opportunity to practice every learning objective in the course on live machines and vulnerable targets. Pre-loaded with over 3,500 hacking tools and a variety of operating systems, you will gain unprecedented exposure to and hands-on experience with the most common security tools, latest vulnerabilities, and widely used operating systems on the market. Our range is web accessible, allowing you to study and practice from anywhere with a connection.
How You Will Get Certified
Prove Your Skills and Abilities With Online, Practical Examinations





How You Will Engage
The C|EH v12 program helps you develop real-world experience in ethical hacking through the hands-on C|EH practice environment. C|EH Engage equips you with the skills to prove that you have what it takes to be a great ethical hacker.
Your security assessment objectives will be presented as a series of flags (questions you must answer in the Cyber Range by performing ethical hacking activities on the target organization).
New to C|EH v12, students will embark on their first emulated ethical hacking engagement. This 4-phase engagement requires students to think critically and test the knowledge and skills gained by capturing a series of flags in each phase, demonstrating the live application of skills and abilities in a consequence-free environment through EC-Council’s new Cyber Range.
As you complete your training and hands-on labs, C|EH Engage lets you apply everything you have learned in a mock ethical hacking engagement. This 4-part security engagement gives you a real ethical hacking engagement experience from start to finish against an emulated organization. Using our capture-the-flag-style range, you will complete your engagement by answering “flag” questions as you progress.

Where You Will Compete
The C|EH Global Challenges occur every month, providing capture-the-flag style competitions that expose students to various new technologies and platforms, from web applications, OT, IoT, SCADA, and ICS systems to cloud and hybrid environments. Our Compete structure lets ethical hackers fight their way to the top of the leaderboard each month in these 4-hour curated CTFs. Objective-based flags are designed around the ethical hacking process, keeping skills current, testing critical thinking abilities, and covering the latest vulnerabilities and exploits as they are discovered. Hosted 100% online in EC-Council’s Cyber Range, candidates race the clock in scenario-based engagements against fully developed network and application environments with real operating systems, real networks, tools, and vulnerabilities to practice, engage, compete, build, and hone their cyber skills against various new target organizations.
New Challenges Every Month

- Learn
- Certify
- Engage
- Compete
What You Will Learn
C|EH is divided into 20 modules and delivered through a carefully curated training plan that typically spans across 5 days. As you progress through your training, each module offers extensive hands-on lab components that allow you to practice the techniques and procedures taught in the program in real-time on live machines.
Ethical Hacking Labs
With over 220 hands-on labs, conducted in our cyber range environment, you will have the opportunity to practice every learning objective in the course on live machines and vulnerable targets. Pre-loaded with over 3,500 hacking tools and a variety of operating systems, you will gain unprecedented exposure to and hands-on experience with the most common security tools, latest vulnerabilities, and widely used operating systems on the market. Our range is web accessible, allowing you to study and practice from anywhere with a connection.
How You Will Get Certified
Prove Your Skills and Abilities With Online, Practical Examinations





How You Will Engage
The C|EH v12 program helps you develop real-world experience in ethical hacking through the hands-on C|EH practice environment. C|EH Engage equips you with the skills to prove that you have what it takes to be a great ethical hacker.
Your security assessment objectives will be presented as a series of flags (questions you must answer in the Cyber Range by performing ethical hacking activities on the target organization).
New to C|EH v12, students will embark on their first emulated ethical hacking engagement. This 4-phase engagement requires students to think critically and test the knowledge and skills gained by capturing a series of flags in each phase, demonstrating the live application of skills and abilities in a consequence-free environment through EC-Council’s new Cyber Range.
As you complete your training and hands-on labs, C|EH Engage lets you apply everything you have learned in a mock ethical hacking engagement. This 4-part security engagement gives you a real ethical hacking engagement experience from start to finish against an emulated organization. Using our capture-the-flag-style range, you will complete your engagement by answering “flag” questions as you progress.

Where You Will Compete
The C|EH Global Challenges occur every month, providing capture-the-flag style competitions that expose students to various new technologies and platforms, from web applications, OT, IoT, SCADA, and ICS systems to cloud and hybrid environments. Our Compete structure lets ethical hackers fight their way to the top of the leaderboard each month in these 4-hour curated CTFs. Objective-based flags are designed around the ethical hacking process, keeping skills current, testing critical thinking abilities, and covering the latest vulnerabilities and exploits as they are discovered. Hosted 100% online in EC-Council’s Cyber Range, candidates race the clock in scenario-based engagements against fully developed network and application environments with real operating systems, real networks, tools, and vulnerabilities to practice, engage, compete, build, and hone their cyber skills against various new target organizations.
New Challenges Every Month

Course Outline
Course Outline
20 Modules that help you master the foundations of
Ethical Hacking and prepare to challenge the CEH certification exam.
20 Modules that help you master the foundations of Ethical Hacking and prepare to challenge the CEH certification exam.
Learn how to use the latest techniques and tools to perform foot printing and reconnaissance, a critical pre-attack phase of the ethical hacking process.
Over 30 hands-on exercises with real-life simulated targets to build skills on how to:
- Perform foot printing on the target network using search engines, web services, and social networking sites
- Perform website, email, whois, DNS, and network foot printing on the target network
Over 10 hands-on exercises with real-life simulated targets to build skills on how to:
- Perform host, port, service, and OS discovery on the target network
- Perform scanning on the target network beyond IDS and firewall
Over 20 hands-on exercises with real-life simulated targets to build skills on how to:
- Perform NetBIOS, SNMP, LDAP, NFS, DNS, SMTP, RPC, SMB, and FTP Enumeration
Over 5 hands-on exercises with real-life simulated targets to build skills on how to:
- Perform vulnerability research using vulnerability scoring systems and databases
- Perform vulnerability assessment using various vulnerability assessment tools
Over 25 hands-on exercises with real-life simulated targets to build skills on how to:
- Perform Online active online attack to crack the system’s password
- Perform buffer overflow attack to gain access to a remote system
- Escalate privileges using privilege escalation tools
- Escalate privileges in linux machine
- Hide data using steganography
- Clear Windows and Linux machine logs using various utilities
- Hiding artifacts in Windows and Linux machines
Get an introduction to the different types of malware, such as Trojans, viruses, and worms, as well as system auditing for malware attacks, malware analysis, and countermeasures.
Over 20 hands-on exercises with real-life simulated targets to build skills on how to:
- Gain control over a victim machine using Trojan
- Infect the target system using a virus
- Perform static and dynamic malware analysis
Learn about packet-sniffing techniques and how to use them to discover network vulnerabilities, as well as countermeasures to defend against sniffing attacks.
Over 10 hands-on exercises with real-life simulated targets to build skills on how to:
- Perform MAC flooding, ARP poisoning, MITM and DHCP starvation attack
- Spoof a MAC address of Linux machine
- Perform network sniffing using various sniffing tools
- Detect ARP poisoning in a switch-based network
Learn social engineering concepts and techniques, including how to identify theft attempts, audit human-level vulnerabilities, and suggest social engineering countermeasures.
Over 4 hands-on exercises with real-life simulated targets to build skills on how to:
- Perform social engineering using Various Techniques
- Spoof a MAC address of a Linux machine
- Detect a phishing attack
- Audit an organization’s security for phishing attacks
Learn about different Denial-of-Service (DoS) and Distributed DoS (DDoS) attack techniques, as well as the tools used to audit a target and devise DoS and DDoS countermeasures and protections.
Over 5 hands-on exercises with real-life simulated targets to build skills on how to:
- Perform a DoS and DDoS attack on a target host
- Detect and protect against DoS and DDoS attacks
Understand the various session hijacking techniques used to discover network-level session management, authentication, authorization, and cryptographic weaknesses and associated countermeasures.
Over 4 hands-on exercises with real-life simulated targets to build skills on how to:
- Perform session hijacking using various tools
- Detect session hijacking
Get introduced to firewall, intrusion detection system, and honeypot evasion techniques; the tools used to audit a network perimeter for weaknesses; and countermeasures.
Over 7 hands-on exercises with real-life simulated targets to build skills on how to:
- Bypass Windows Firewall
- Bypass firewall rules using tunneling
- Bypass antivirus
Over 8 hands-on exercises with real-life simulated targets to build skills on how to:
- Perform web server reconnaissance using various tools
- Enumerate web server information
- Crack FTP credentials using a dictionary attack
Over 15 hands-on exercises with real-life simulated targets to build skills on how to:
- Perform web application reconnaissance using various tools
- Perform web spidering
- Perform web application vulnerability scanning
- Perform a brute-force attack
- Perform Cross-Site Request Forgery (CSRF) Attack
- Identify XSS vulnerabilities in web applications
- Detect web application vulnerabilities using various web application security tools
Over 4 hands-on exercises with real-life simulated targets to build skills on how to:
- Perform an SQL injection attack against MSSQL to extract databases
- Detect SQL injection vulnerabilities using various SQL injection detection tools
Over 3 hands-on exercises with real-life simulated targets to build skills on how to:
- Foot Print a wireless network
- Perform wireless traffic analysis
- Crack WEP, WPA, and WPA2 networks
- Create a rogue access point to capture data packets
Over 5 hands-on exercises with real-life simulated targets to build skills on how to:
- Hack an Android device by creating binary payloads
- Exploit the Android platform through ADB
- Hack an Android device by creating APK file
- Secure Android devices using various Android security tools
Over 2 hands-on exercises with real-life simulated targets to build skills on how to:
- Gather information using Online foot printing tools
- Capture and analyze IoT device traffic
Over 5 hands-on exercises with real-life simulated targets to build skills on how to:
- Perform S3 Bucket enumeration using various S3 bucket enumeration tools
- Exploit open S3 buckets
- Escalate IAM user privileges by exploiting misconfigured user policy
Over 10 hands-on exercises with real-life simulated targets to build skills on how to:
- Calculate MD5 hashes
- Perform file and text message encryption
- Create and use self-signed certificates
- Perform email and disk encryption
- Perform cryptanalysis using various cryptanalysis tools
Common Job Roles for C|EH
Mid-Level Information Security Auditor
Cybersecurity Analyst level 1, level 2, & level 3
Cybersecurity Auditor
Network Security Engineer
Security Administrator
SOC Security Analyst
IT Security Administrator
Security Analyst
Cyber Defense Analyst
Network Engineer
Vulnerability Assessment Analyst
Senior Security Consultant
Warning Analyst
Information Security Manager
Information Security Analyst 1
Senior SOC Analyst
Security Analyst L1
Solution Architect
Infosec Security Administrator
Cybersecurity Consultant
Common Job Roles for C|EH


Making an informed decision is difficult, and that’s where EC-Council’s C|EH brochure comes to your rescue. The Certified Ethical Hacker (CEH) credential is the most trusted ethical hacking certification that employers worldwide value, and for good reasons.
The comprehensive curriculum covers the fundamentals of ethical hacking, foot printing and reconnaissance, scanning, enumeration, vulnerability threats, social engineering, SQL injection, and much more.
When you successfully achieve the C|EH certification, you will be equipped with every skill you need to uncover vulnerabilities and secure the systems, networks, applications, databases, and critical data from malicious hackers.
This is only an overview of C|EH and what you will learn.
For complete information, download the brochure now.

Is This Course For Me?
We have helped over 250,000 people answer this question over the past 20 years and we are excited to help you with this big decision! Choosing the right credential can seem like a difficult task, here are some things you should consider:
- C|EH v12 Program
- Certification Questions
- C|EH v12 Training
- C|EH v12 Accreditation
Certified Ethical Hackers are hired by organization’s either on contract or as full-time employees to help improve the organizations security posture. C|EH is a required baseline certification for many different job roles, but the function of ethical hacking itself involves a methodical practice of identifying, evaluating, testing, and reporting on vulnerabilities in an organization. Ethical Hacking is a broad practice that covers many different technologies, but by systematically applying the methodologies taught in the C|EH program, ethical hackers can evaluate nearly any application or infrastructure they are tasked with, identify potential vulnerabilities, and provide recommendations on how those vulnerabilities can be remediated. In the case of military organizations, ethical hackers are highly trained in offensive and defensive activities and possess the critical skill sets and tactics to evaluate target systems and defend their own organization’s assets in real time.
While this is very much a personal decision for most, holding a C|EH certification communicates to your potential or current employer that you possess the baseline knowledge and skills to be an effective and productive member of the security team. The field of cybersecurity is rapidly growing with projected Job opportunity growth of 33%, according to U.S. Department of Labor, globally there is an insufficient supply of qualified people creating amazing opportunities for Certified Ethical Hackers in nearly every industry. To read more about the impact of C|EH on many of our Hall of Fame Ethical Hackers, read our Hall of Fame report here: https://www.eccouncil.org/ceh-hall-of-fame/
Considering the global need and lack of qualified talent in the workforce, cybersecurity professionals are paid exceptionally well in most cases. As of August 2022, a simple search in Salary.com for United States based positions show that Certified Ethical Hackers make an average of $103,866 per year, with the 90th percentile earning above $130,000. Experience, education levels, and other certifications provide even more value in most cases, but it is common to see starting salaries for Ethical Hackers that stretch well into six figures. We recommend searching your local job boards, viewing local salary information, and talking to potential employers to assess your own value in the market. C|EH has been ranked in the top 5 highest paid cybersecurity certifications for the last 10 years and continues to grow worldwide. Don’t just trust us though-here are a few examples so you can see what other research has concluded:
- https://www.zdnet.com/education/computers-tech/best-ethical-hacking-certification
- https://www.roberthalf.com/blog/salaries-and-skills/which-it-certifications-are-most-valuable
- https://www.infosec-careers.com/the-best-cyber-security-certifications-in-2022/
- https://www.cio.com/article/193586/top-15-it-certifications-in-demand-for-2021.html
- https://www.enterprisestorageforum.com/manage-ment/cybersecurity-certifications/
The C|EH Exam is an ANSI 17024 exam which means it goes through extensive external validation to ensure the examination itself is fair for the knowledge and experience level of our certification challengers. With the recommendation of 2 years’ experience in IT Security or 0fficial training, candidates attempting the exam need to possess strong knowledge in computing systems, networks, and a variety of other IT topics. The examination itself uses Cut-Scores to determine pass/fail results and cut scores are carefully set by psychometricians who regularly evaluate test question performance and average pass/fail results throughout the life of the program. Reviews from our certification members with limited experience or background have rated our exam as difficult, while more seasoned IT and IT security professionals rate the exam as moderately challenging even after official training. You may review the exam domains and the exam blueprint here to learn more: https://cert.eccouncil.org/certified-ethical-hacker.html
1. Attend official training through our online learning provided by iClass, through an Authorized Training Center (ATC) located in 140+ countries around the world, or at a college or university that is also an official EC-Council Academia Partner. All candidates attending official training at an official EC-Council partner if deemed eligible to attend the training will have direct access to the examination which can be proctored at the training center, online using EC-Council’s remote proctoring service, or at over 4,500 VUE testing centers across the world.
2. Eligibility Application – If you possess the experience and don’t feel training is necessary in the domains of the exam, you may wish to skip the training and go straight to challenging the exam. If you do not attend official training, you will need to apply for exam eligibility here: https://cert.eccouncil.org/application-process-eligibility.html. After the application is processed and approved, EC-Council will work directly with you to determine the best delivery method for the exam, and you may then challenge the 4-hour certification exam as scheduled.
Masterclass provides student with a Live Online, Instructor led class schedule with set times where our award-winning instructors will guide you through the C|EH training module by module incorporating hands on lab time, breakout sessions for discussions and a live presentation of all course materials.
iLearn is EC-Councils On-Demand training option. We have hand selected the best instructors, flown them to our Albuquerque based studio and produced professional pre-recorded video lectures and lab walkthroughs that can be accessed through your iClass student account any time, 24x7x365.
(UK’s intelligence, security, and cyber agency) Approves EC-Council Training as meeting CYBOK requirements.
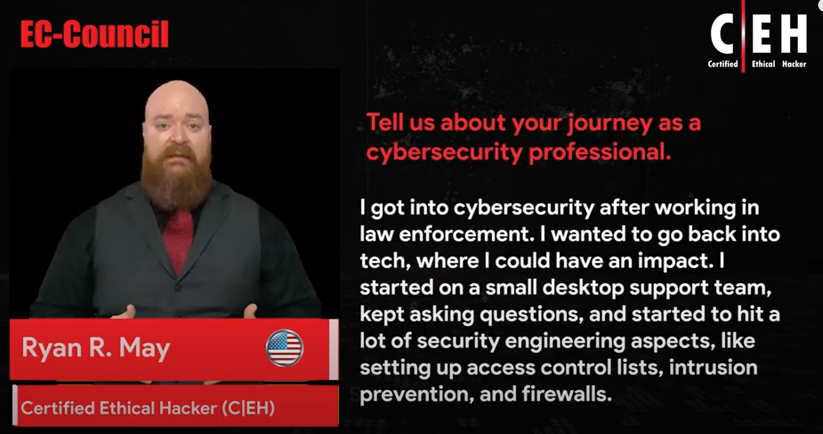
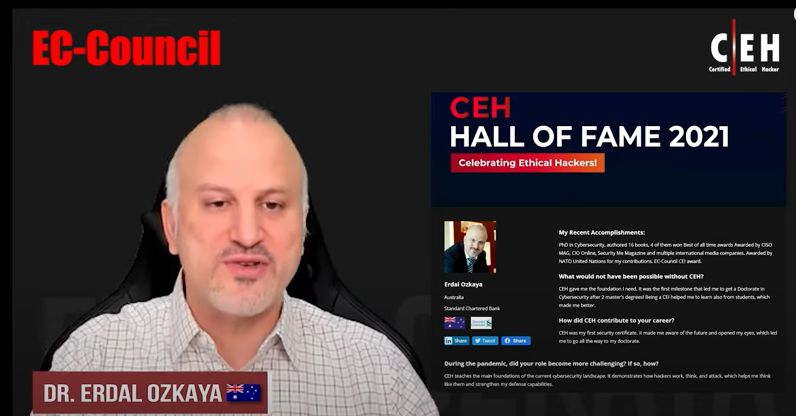
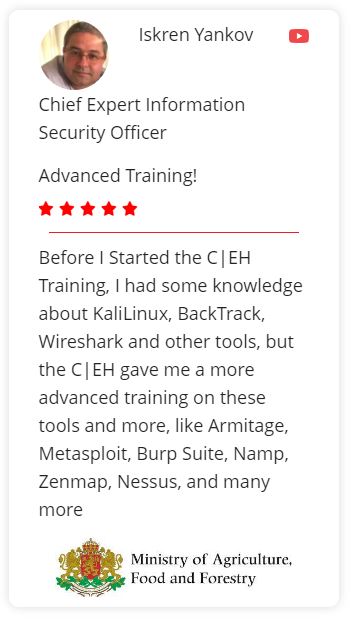
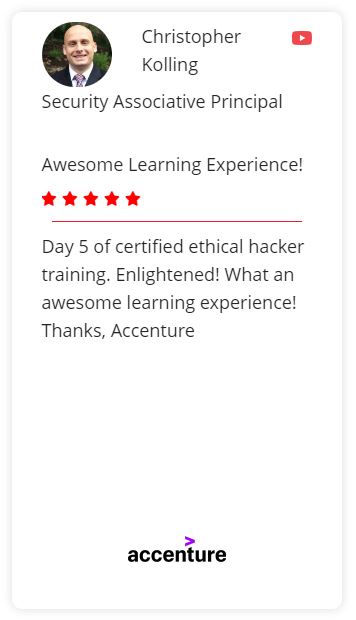
Discover Why C|EH Trusted By Organization Across The World!
For more than 10 years, Cybertechinfosolutions cybersecurity programs have empowered cybersecurity professionals around the world to exercise their training and expertise to combat cyberattacks. The Hall of Fame celebrates those individuals who have excelled, achieved, and fostered a spirit of leadership among their colleagues and peers within the cyber community.
97 %
Rated the program topics as directly relevant to current real-world threats.
63 %
Reported a direct pay raise or promotion after attaining their C|EH certification.
95 %
Reported being able to improve organizational security after completing the program.